Authentication
docuteam box has two different authentication mechanisms, one for the user interface and one for the API.
User interface
Authentication for the user interface is managed using a Keycloak instance. Users are either managed directly in this instance, or using an external identiy provider using OpenID Connect or SAML 2.0 (e.g. AzureAD).
The table below lists the available roles and their associated permissions.
| Role | Simple search | Edit record resource | Display Cockpit | Use SPARQL search | API keys | Webhooks | Tasks | Features | Settings | Maintenance |
|---|---|---|---|---|---|---|---|---|---|---|
| admin | X (all namespaces) | - | X (all namespaces) | - | X | X | X (all) | X | X | X |
| <namespace>@user | X (only <namespace>) | - | X (only <namespace>) | - | - | - | X (own) | - | - | - |
| <namespace>@editor_metadata | - | X (only <namespace>) | - | - | - | - | - | - | - | - |
| sparql_query | - | - | - | X | - | - | - | - | - | - |
API
Requests to the API are authenticated with an X-Auth-Token header. The actual tokens are managed through the user interface:
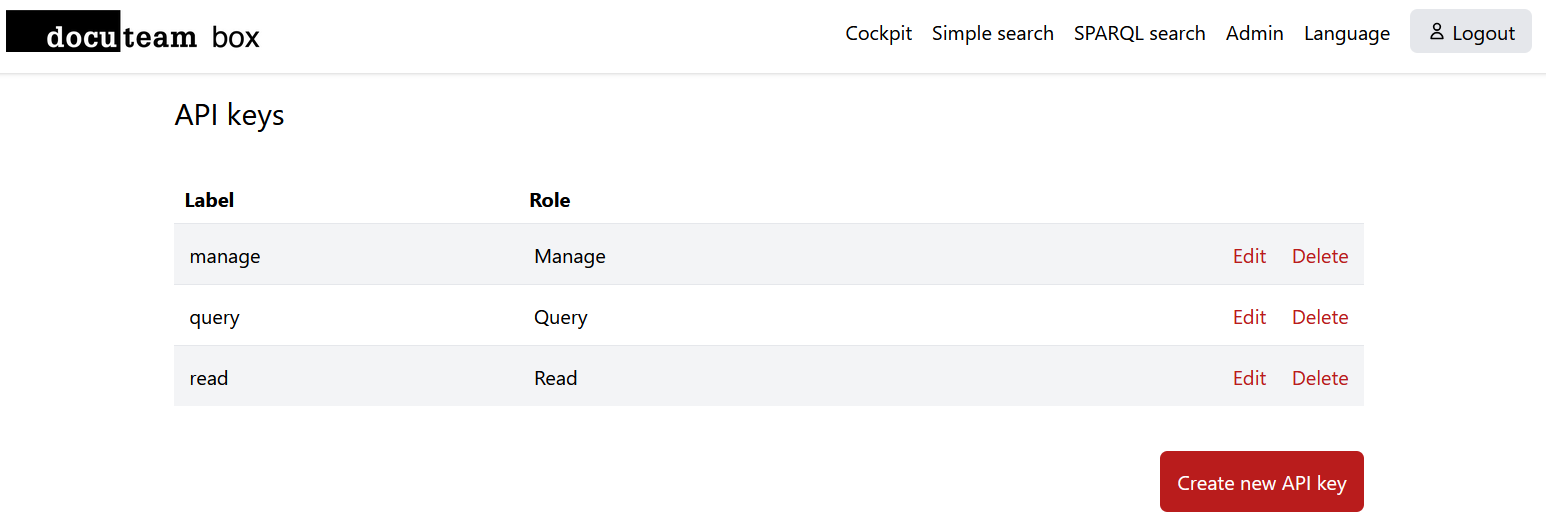
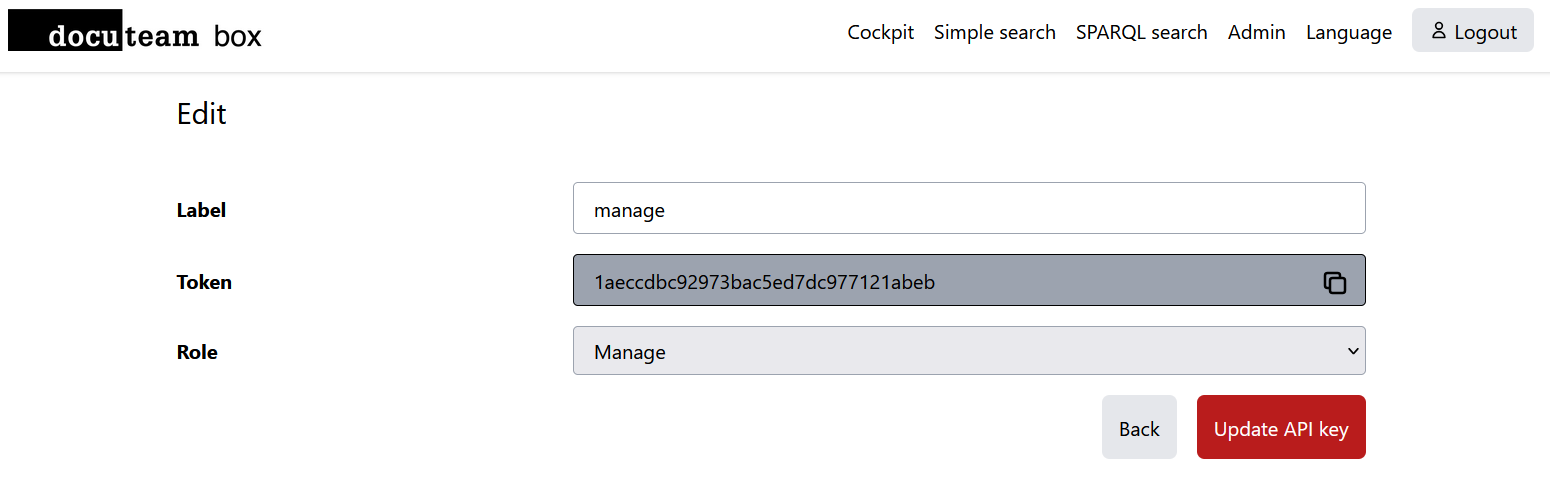
Each key has the following properties:
- Choose a
labelto easier remember the usage/context of the token. - The
tokenis generated automatically when creating a new API key. - The
roleis eitherRead,QueryorManage:Readpermits access to objects specific endpoints, i.e. getting previews, originals or entire DIPsQueryadditionally allows overall search in the repository using the triplestore.Manageadditionally allows changing data in Fedora by using the insert and replace API.